System and Data security
This document serves as an overview of SumUp POS (ex Goodtill) data security – more detailed documentation is available on request.
Architecture
SumUp POS provides several applications and services for Point of Sale. See the diagram below for an overview of the system architecture: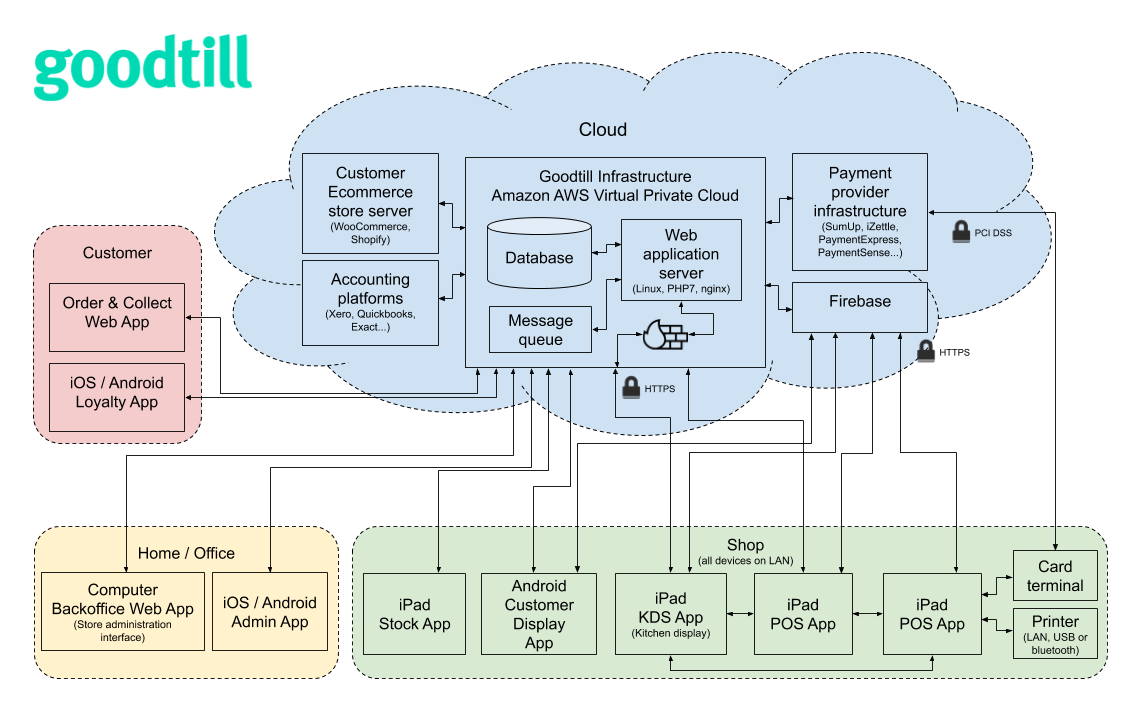
Cloud and data security
Goodtill has obtained PCI DSS SAQ-D compliance valid from July 2019 to July 2024. This certification required an assessment of the cloud infrastructure and apps listed in the architecture diagram above.
Goodtill’s backend system is hosted in the cloud within Amazon’s secure data centres in Northern Ireland (eu-west-1 region).
The AWS shared security model states that Amazon is responsible for the availability and physical security of the services they provide (compute, databases, networking etc) and the customer (Goodtill) is responsible for ensuring that these services are used securely (eg the code running on the services and configuration of the services is secure).
AWS has obtained CSA STAR Level 2 and ISO 27001 certifications.
Goodtill’s applications communicate with the central database via an HTTPS API. Data is always encrypted when transported over WAN (eg between POS app clients and our servers) using TLS1.2 over HTTPS (as required by PCI). Data in the database itself is not encrypted at rest.
The POS app includes support for syncing data between other POS devices on the LAN. This communication is not encrypted however the data does not include personal information (only customer IDs, sale items etc) and this feature can be disabled.
Application security
SumUp POS's POS app runs on Apple’s iOS operating system. The security model of iOS utilises sand boxing to prevent apps from reading data stored by other apps, therefore all POS data is stored safely on the device.
Customers are responsible for keeping the operating system of their devices and SumUp POS's applications up to date, however Goodtill can offer MDM (Mobile Device Management) services to automatically deploy app updates to iOS devices in large deployments.
Access controls
Permissions
Goodtill stores contain two databases of user records.
- Users
- Allows access to the backoffice and POS app (depending on their role).
- Authenticated using subdomain, username and password.
- Provided to store owners and trusted members of staff.
- Allowed access to one or more outlets.
- Granted all permissions or a subset of permissions.
- Staff
- Used to authenticate the user within the POS app (after login with user account).
- Authenticated using a 4-6 digit PIN.
- Provided to every till operator.
- Allowed access to one or all outlets.
- Granted all permissions (manager status) or a subset of permissions.
Passwords
Password composition is required to be PCI-compliant – Minimum 7 characters, at least 1 letter (either case), at least 1 number.
Passwords are stored using a secure one-way has function (bcrypt). Automated protections are in place to prevent passwords being stored in log files.
Currently only single-factor authentication is supported, however support for two-factor authentication is planned.
Login attempts are rate limited to 50 unsuccessful attempts per 5 minutes per IP address. This blocks attempts from the IP address, not login attempts for the user account.
After a successful login attempt, users are granted an access token which is valid for 2 weeks. The life of the access token is extended indefinitely by refreshing it as long as it being used, two weeks after the last refresh the token can no longer be used or refresh. This token is invalidated if the user logs out of their session. Users can log out of all sessions to invalidate all previously granted access tokens.
Support access
Goodtill staff may gain access to customer Backoffice systems via our internal management system. Access is only permitted to users operating in a support capacity and an access to client stores is recorded in the audit log.
Auditing
Goodtill’s system records audit logs for changes to sensitive data within a store. Changes considered sensitive include payment processor details, integration credentials and changes to some store data (eg product prices). These records are stored indefinitely.
Each audit record contains the following:
- Store user
- Reference to updated record
- Values before and after the update
- IP address
- User agent
- Session ID
If the change was made by a member of Goodtill staff accessing a store, their staff ID will also be stored.
This data is not currently available for store owners access and is instead used by Goodtill staff only used to investigate incidents.
Payment and personal data security
Payment data
Goodtill does not store CHD (cardholder data) as defined by the PCI council (full 16 digit PAN). Goodtill never has access to the full PAN as it is not provided to us by any of our integrated payment methods. Goodtill will store other card details such as the 4 last digits and expiry date if provided to us by the payment provider.
Goodtill supports the following payment providers:
- SumUp
- Zettle
- PaymentSense/Dojo
If you require any details regarding the security certifications and P2PE support available for these products we advise contacting the payment providers directly, as certifications and support are subject to change.
Personal data
The Goodtill system includes a customer management module where store owners can maintain a database of their customers. Customers can be managed on the backoffice and registered and assigned to sales within the POS app. Usage of this feature is optional unless you are using our Click & Collect module or Goodies applications which require the user to signup. The following table lists the customer data recorded in each use case:
| Use case | Data collected |
|---|---|
| POS Signup | The store owner can populate any fields necessary, there are no required fields. |
| Goodies application |
|
| Goodeats web application |
|
Goodtill has implemented systems which allow end users to request the following under the GDPR:
- Subject Access Request – This will email the user a copy of their data held in Goodtill’s systems (such as personal information and sales records).
- Deletion request – This will remove their personal data for their record in the database.
An Incident Response policy is in place, this includes notifying all relevant stakeholders including the affected customers and the ICO within 72 hours.